A new report by Agari and PhishLabs of HelpSystems, LLC, suggests that sales of stolen information is shifting away from carding marketplaces on the darknet to chat-based services, which accounted for 45% of all stolen data sales in Q2 2022. The findings are in line with the shutdown or retirement of some major darknet carding sites in the first quarter of the year, with UniCC voluntarily closing shop in mid-January and SSNDOB being seized by the FBI in early June.
The stolen information analyzed in the report, which encompasses hundreds of thousands of attacks recorded in Q2 2022, is mostly obtained through phishing and social media attacks that largely target banks, credit unions, telecoms, and financial services providers. According to HelpSystems, credit card data (often referred to as “fullz”) remains the “most common threat advertised by criminals” on the dark web, with sales increasingly taking place in private chat sessions rather than via darknet market advertisements.
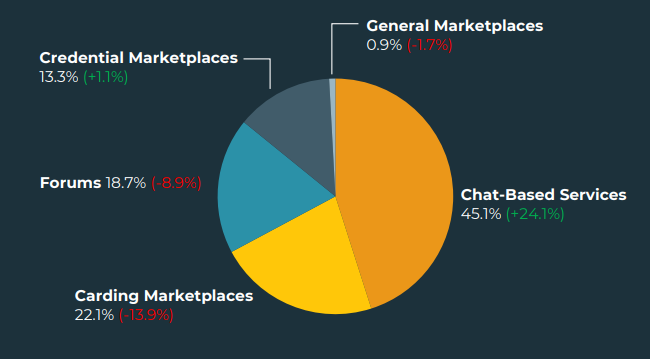
A breakdown of the shift in sales of stolen data on the darknet in Q2 2022. Source: PhishLabs
The report also noticed a substantial rise in the number of “hybrid vishing” attacks between Q1 2021 and Q2 2022. These are multi-pronged phishing attacks that usually begin with a victim receiving an email in which there is a phone number that appears to be from a legitimate source. The victim is lured to call the number through the content of the email, with attackers on the other side of the line attempting to “vish” sensitive information out of the victim.
“Threat actors are taking advantage of new and uncommon methods to maximize attack effectiveness,” writes Tripwire author PJ Bradley in a summary of the report by PhishLabs. “Hybrid vishing attacks seen in Q2 are a prominent example of cybercriminals modifying tactics to circumvent security measures,” they conclude.
A key takeaway from the report is the finding that phishing attacks have been steadily rising in 2022, with social media attacks increasing over 100% during the last 12 months. The report also found that Emotet trojan horse virus now represents almost 50% of malware payload attacks and that 60% of credential theft phishing attacks target Office 365 credentials, which are seemingly the most lucrative of online credentials.